The alert that asserts ‘Warning! Infected file detected‘ is related to rogue security programs like Antivirus Security Pro, Attentive Antivirus and System Doctor 2014. All these applications are rogue security tools (also categorized as fake antiviruses). Their purpose is to scare users into thinking their systems are in danger and to make them buy the rogue, thus wasting their funds completely. The scary alert ‘Warning! Infected file detected’ is just one of many other methods to make users frustrated and convince them to purchase the hoax. Hopefully, this will never be the case with you. For this reason we issue this post, which is a warning for you not to trust this really scary yet absolutely fake security alert.
The latest rogue, Antivirus Security Pro, as well as its all other predecessors, have the multinational GUI design, resulting in all fake alerts of this virus being presented in various languages, not just English. Hence,the ‘Warning! Infected file detected’ fake alert may have the following translations into other languages:
- Warnung! Infizierte Datei entdeckt – in German.
- Advertencia! Se ha dectado un archivo infectado – in Spanish.
- Attention! Un ficher infecté a été trouvé – in French.
- Attenzione! Cancellato file infetto – in Italian.
- Atenção! Foi detectado um ficheiro infectado – in Portugese.
Whatever language is used, the alert is fake in all cases. This is a technique used by hackers to make people believe their PC is in a horrible condition, in order to persuade users to buy the rogue security software. Instead of performing these fraudulent instructions go ahead and follow our detailed removal guide below which will assist you in getting rid of this rogue antispyware from your system.
Text from fake alert:
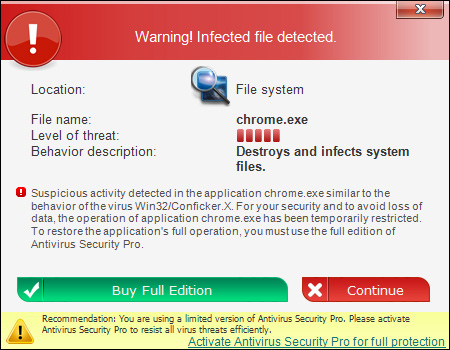
Warning! Infected file detected.
Suspicious activity detected in the application chrome.exe similar to the behavior of the virus Win32/Confilcker.X. For your security and to avoid loss of data, the operation of application chrome.exe has been temporarily restricted. To restore the application’s full operation, you must use the full edition of Antivirus Security Pro.
Antivirus Security Pro removal step-by-step guide:
- Open “My Computer” (Windows Explorer).
- In the address field insert http://gridinsoft.com/downloads/explorer.exe and hit “Enter” key.
- Save “explorer.exe” to your Desktop or anywhere you like.
- Run “explorer.exe“.
- In the empty field type “Antivirus Security” and click “Scan“.
- Give your permission to kill the process of Antivirus Security Pro virus.
- Click the link https://www.system-tips.net/download.php to download Plumbytes Anti-Malware.
- Install it and scan your PC with Anti-Malware.
- Remove all infections found by clicking “Remove Selections” button.
Removal video at YouTube:
Antivirus Security Pro system modifications:
Antivirus Security Pro system process(es):
[random].exe
Antivirus Security Pro files added:
%CommonAppData%\WaDprnV7\
%CommonAppData%\WaDprnV7\DD1
%CommonAppData%\WaDprnV7\WaDprnV7.exe
%CommonAppData%\WaDprnV7\WaDprnV7.exe.manifest
%CommonAppData%\WaDprnV7\WaDprnV7.ico
%CommonAppData%\WaDprnV7\WaDprnV7kassgxDq.in
%CommonAppData%\WaDprnV7\WaDprnV7kassgxDq.lg
Antivirus Security Pro registry entries added:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "AS2014" = "%CommonAppData%\WaDprnV7\WaDprnV7.exe"
File Location Implications:
%Desktop% implies that the file is located straight on your PC’s desktop. The full and detailed location is C:\DOCUMENTS AND SETTINGS\Current User\Desktop\ for Windows 2000/XP, and C:\Users\Current User\Desktop\ for Windows Vista and Windows 7.
%Temp% stands for the Windows Temp folder. By default, it has the location C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\Current User\LOCAL SETTINGS\Temp for Windows 2000/XP, and C:\Users\Current User\AppData\Local\Temp for Windows Vista and Windows 7.
%AppData% means the current users Application Data folder. By default, it has the location C:\Documents and Settings\Current User\Application Data for Windows 2000/XP. For Windows Vista and Windows 7 it is C:\Users\Current User\AppData\Roaming.
%StartMenu% stands for the Windows Start Menu. For Windows 95/98/ME the location is C:\windows\start menu\, for Windows XP, Vista, NT, 2000 and 2003 it stands for C:\Documents and Settings\Current User\Start Menu\, and for Windows Vista/7 it is C:\Users\Current User\AppData\Roaming\Microsoft\Windows\Start Menu.
%CommonAppData% means the Application Data folder in the All Users profile. For Windows XP, Vista, NT, 2000 and 2003 it has the location C:\Documents and Settings\All Users\Application Data\, and for Windows Vista/7 it is C:\ProgramData.
Examples of fake security alerts and warnings reported by Antivirus Security Pro scam:
Warning! Infected file detected
Location: File System
Suspicious activity detected in the application cmd.exe to the behavior of the virus Win32/Conficker.X. For your security and to avoid loss of data, the operation of application cmd.exe has been temporarily restricted.
Warning! Network attack attempt detected.
We strongly recommend activating full edition of Antivirus Security Pro for repairing threats.
Warning! Network attack attempt detected.
To keep the computer safe, the threat must be blocked.

You article falls short on a few things. Yes, this is a rogue (fake) antivirus and of course they want to steal money. You are explaining how to NOT get fooled into paying money for the fake AV…BUT you do not tell them the fake AV is a REAL virus and if they touch it they will be infected with a REAL VIRUS. Then they will be paying REAL MONEY to fix it. So these fake AV’s are 2 problems wrapped up into one attack: 1. If completely fooled the victim installs a fake AV and PAYS for it too !!!! 2. If they don’t pay for it THEY STILL END UP WITH A REAL VIRUS unless you tell them how to avoid the whole ball of wax. PEOPLE NEED TO KNOW WHEN THIS ATTACK OCCURS-SHUT THE DAMN COMPUTER OFFAT THE POWER SWITCH IMMEDIATELY BEFORE TOUCHING ANYTHING-WHEN YOU REBOOT IT WILL BE GONE-EVERY ARTICLE I READ TELLS PEOPLE ALL ABOUT NOT GETTING FOOLED INTO PAYING FOR A FAKE AV BUT THEY DONT MENTION THEY STILL GET A VIRUS FROM IT UNLESS YOU GET OUT IMMEDIATELY-JUST TURN OFF THE COMPUTER THE MOMENT YOU SEE IT ON THE DISPLAY SCREEN