These instructions will help you to remove Windows AntiBreach Helper virus from your computer. If you try to uninstall it in a regular manner you will not even find this program in the list of installed software. Why is it so? The answer to this question is quite simple, by the way. This is because Windows Anti Breach Helper is a rogue antispyware, and it doesn’t use legal ways of infiltration into computers.
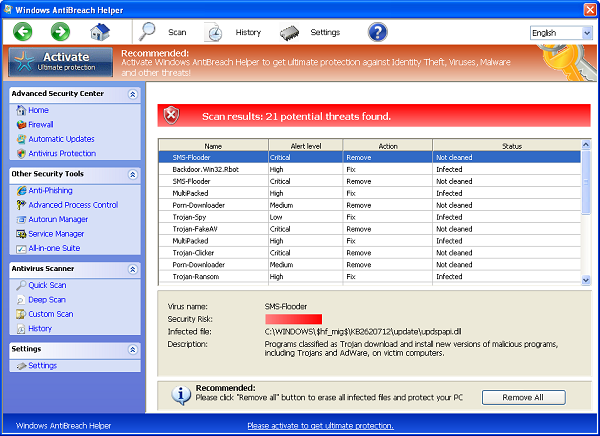
Windows Anti Breach Helper virus gets into PCs by means of fake Microsoft Security Essentials Alerts. As a matter of fact, these fake MSE warnings mainly pop-up through several vulnerabilities available with your browser. This problem, however, is mainly particular to browsers like Internet Explorer, Mozilla Firefox and Google Chrome.
Fake Microsoft Security Essentials Alerts on vulnerable PC generally report some fake problem or unreal infection supposedly dwelling on the PC. As a solution to fix the issue, this fake MSE warning tells users to download some tool to scan PC, detect the threats and delete it. So, if user actually agrees to download this “tool”, this is when he/she actually downloads and installs Windows Anti-Breach Helper.
Unlike security services rendered by real Microsoft Security Essentials software, Windows AntiBreach Helper always asks for money from users. However, it cannot render any decent services for computers. The problems it reports are all fake, the threats it supposedly identifies during the fake system scan are all invented.
Please don’t waste your money, do not buy the so-called “ultimate protection” of Windows AntiBreach Helper rogue antivirus. Instead, you definitely need to get rid of this malware program from your computer. Please carefully follow the removal instructions provided in the rest of this article.
Software necessary for Windows AntiBreach Helper virus removal:
Windows AntiBreach Helper removal steps:
- In Windows AntiBreach Helper click “?” Menu button anc click “Register”:
- Paste this product key – 0W000-000B0-00T00-E0022 exactly as shown at the image below, then click “Register“:
- 0W000-000B0-00T00-E0001
- 0W000-000B0-00T00-E0002
- 0W000-000B0-00T00-E0003
- 0W000-000B0-00T00-E0021
- Afer registration download Plumbytes Anti-Malware without any restrictions on the part of the rogue, scan your PC with Plumbytes Anti-Malware and remove all infections detected by clicking “Apply” button at the end of scan.
- Restart your computer and repeat scan.


Note! If this product key has been found to be invalid, try one of these keys as well:
Windows AntiBreach Helper similar removal video at YouTube:
Beware of ways how Windows AntiBreach Helper is spread today:
Windows AntiBreach Helper uses various vulnerabilities of browsers like Internet Explorer, Google Chrome, Mozilla Firefox, Opera and many others for the interference into your computer. For example, you might get the following scary alert, supposedly coming from Microsoft Antivirus:
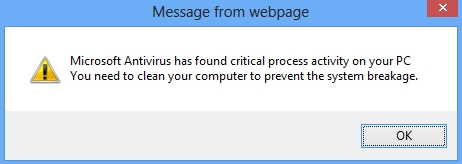
Microsoft Antivirus has found critical process activity on your PC. You will need to clean your computer to prevent the system breakage.
If you actually click the “OK” button as shown at the image you will have another fake alert, not associated at all to Microsoft Security Essential Alert, but yet claiming to be such:
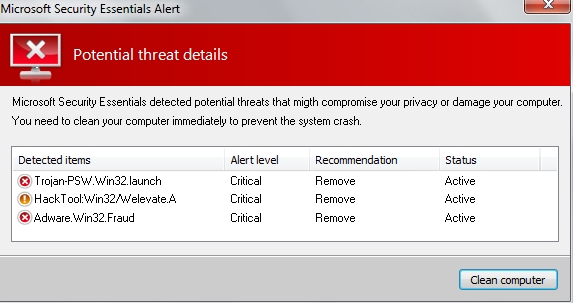
Microsoft Security Essentials Alert
Potential threat details
Microsoft Security Essentials detected potential threats that might compromise your privacy or damage your computer. You need to clean your computer immediately to prevent the system crash.
Detected items:
– Trojan-PSW.Win32.launch
– HackTool:Win32/Welevate.A
– Adware.Win32.Fraud
Associated files and registry entries:
Related files:
%AppData%\svc-[rnd].exe
%CommonAppData%\connector.swf
%Programs%\Windows AntiBreach Helper.lnk
%Desktop%\Windows AntiBreach Helper.lnk
Related registry entries:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\PrSft %AppData%\svc-[rnd].exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\k9filter.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\k9filter.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe\Debugger svchost.exe
Fake security alerts, notifications and warnings of Windows AntiBreach Helper scam:
Firewall has blocked a program from accessing the Internet
C:\Program Files\Internet Explorer\iexplore.exe
is suspected to have infected your PC.
This type of virus intercepts entered data and transmits them
to a remote server.
Error
Trojan activity detected. System integrity at risk.
Full system scan is highly recommended.
Error
System data security is at risk!
To prevent potential PC errors, run a full system scan.
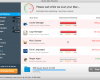
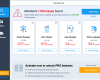
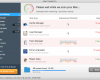

My version of helper froze all my browsers. No registration was present. It went to credit card site and then asked for credit card number charge of $99.9
Any mouse click brought up a pop up telling me I needed to click prevent and that went back to payment window. I am attempting to delete with malware bytes program.