This is the guide explaining Win 7 Security Cleaner Pro fake antivirus removal. Such program is a malicious application that should be immediately deleted from your computer. In this article you will get acquainted with both text removal instructions and video presentation that shows exact elimination process of this scam. Getting rid of this fake AV manually is a time-consuming process. Plus, it requires additional technical computer skills. So, we believe automatic removal of this malware is the best solution for you to choose.
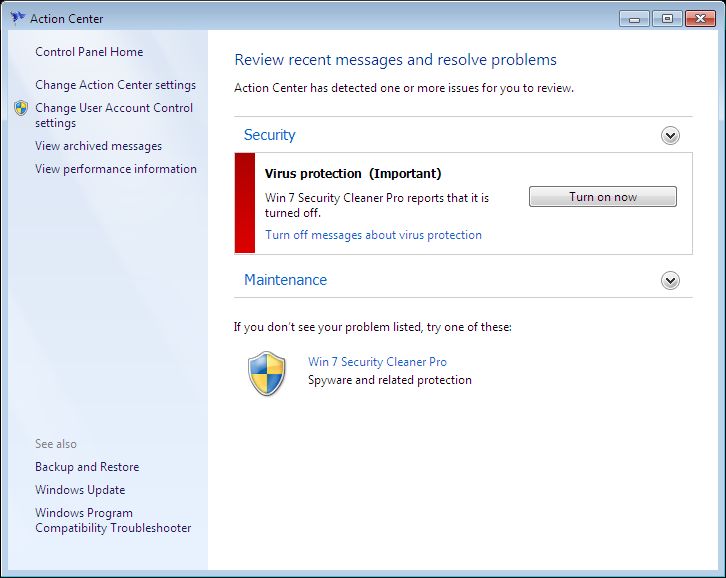
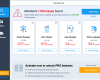
The program you see at the screenshot is rightfully classified as a rogue anti-spyware tool. Its infiltration into attacked computers is concealed. In other words, users never participate in the installation process of this application. Within a couple of seconds after computer being infected with Win 7 Security Cleaner Pro scam this hoax comes up and begins scanning your computer. By the way, it also uses fake Action Center, replacing the legitimate one of Windows operating system. Here is how the rogue AV looks like on a real computer:
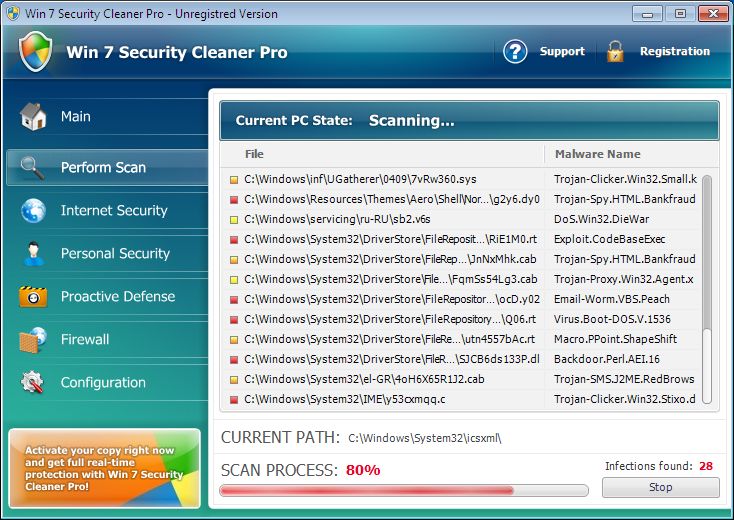
The behavior of Win 7 Security Cleaner Pro isn’t different from that of other rogues. So, the program begins running the fake scanning of your computer. It’s worthy to say that, unlike many other rogues, this scan lasts for quite a continuous period of time. Then the hoax reports the large number of fake infections which aren’t even present on the computer. This is all done in order to make users believe that their system is tremendously infected. Then, of course, the virus program will tell users that they need to purchase its license, which is obviously a fake license that can’t remove real security threats or at least warn users about real malware intrusion attempts.
Considering the above-said, Win 7 Security Cleaner Pro is not a good program to keep on your system. This is the product of cyber hackers who want to trick as many users as possible into buying the rogue security software. So, instead of buying this malware please go ahead and immediately remove this fake AV from your computer.
If you have mistakenly purchased Win 7 Security Cleaner Pro virus then immediately contact your bank or other payment processing institution and dispute the charges that were made through your bank card or account. Tell the bank officials that the program you purchased is a rogue security software. Hopefully, there’s a chance of getting money back. Finally, please follow the guide that explains removal of Win 7 Security Cleaner Pro automatically with the help of Plumbytes Anti-Malware.
Win 7 Security Cleaner Pro removal steps:
- First, ignore all scary alerts of Win 7 Security Cleaner Pro scam.
- Use “Win + E” hotkey command to open Run command window.
- In the address line type the direct download link of Plumbytes Anti-Malware http://trojan-killer.net/download.php and click “Enter“.
- Save the installer of Plumbytes Anti-Malware onto your desktop.
- Right-click the installer with your mouse and run it as Administrator.
- Install Anti-Malware. Uncheck the box “Run Anti-Malware” at the end of installation process.
- Right-click the desktop icon of Plumbytes Anti-Malware and run Anti-Malware as Administrator.
- Update Anti-Malware and run scan with it.
- Once the scanning has been completed, click “Remove Selections” to remove all items associated with Win 7 Security Cleaner Pro.
- Restart your computer and repeat scan if necessary.
- Share this malware removal guide with your colleagues, relatives and friends.
Removal video at YouTube:
Download recommended malware removal solution:
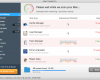
Fake Action Center:
Associated virus files:
%CommonAppData%\[random characters and numbers]
%LocalAppData%\[random characters and numbers]
%LocalAppData%\[random 3 characters].exe
%Temp%\[random characters and numbers]
%AppData%\Roaming\Microsoft\Windows\Templates\[random characters and numbers]
Associated registry entries:
HKEY_CURRENT_USER\Software\Classes\.exe “(Default)” = ‘[random]’
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “(Default)” = “%LocalAppData%\[random 3 characters].exe” -a “%1” %*
HKEY_CLASSES_ROOT\[random]
HKEY_CURRENT_USER\Software\Classes\[random] “(Default)” = ‘Application’
HKEY_CURRENT_USER\Software\Classes\[random]\DefaultIcon “(Default)” = ‘%1’
HKEY_CURRENT_USER\Software\Classes\[random]\shell\open\command “(Default)” = “%LocalAppData%\[random] 3 characters].exe” -a “%1” %*
HKEY_CLASSES_ROOT\.exe\shell\open\command “(Default)” = “%LocalAppData%\[random 3 characters].exe” -a “%1” %*
HKEY_CLASSES_ROOT\ah\shell\open\command “(Default)” = “%LocalAppData%\[random 3 characters].exe” -a “%1” %*
HKEY_CLASSES_ROOT\ah\shell\open\command “IsolatedCommand”
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command “(Default)” = “”%LocalAppData%\[random 3 characters].exe -a “C:\Program Files\Mozilla Firefox\firefox.exe””
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command “(Default)” = “”%LocalAppData%\[random 3 characters].exe” -a “C:\Program Files\Mozilla Firefox\firefox.exe” -safe-mode”
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command “(Default)” = “”%LocalAppData%\[random 3 characters].exe” -a “C:\Program Files\Internet Explorer\iexplore.exe””
File Location Implications:
%Desktop% implies that the file is located straight on your PC’s desktop. The full and detailed location is C:\DOCUMENTS AND SETTINGS\Current User\Desktop\ for Windows 2000/XP, and C:\Users\Current User\Desktop\ for Windows Vista and Windows 7.
%Temp% stands for the Windows Temp folder. By default, it has the location C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\Current User\LOCAL SETTINGS\Temp for Windows 2000/XP, and C:\Users\Current User\AppData\Local\Temp for Windows Vista and Windows 7.
%AppData% means the current users Application Data folder. By default, it has the location C:\Documents and Settings\Current User\Application Data for Windows 2000/XP. For Windows Vista and Windows 7 it is C:\Users\Current User\AppData\Roaming.
%StartMenu% stands for the Windows Start Menu. For Windows 95/98/ME the location is C:\windows\start menu\, for Windows XP, Vista, NT, 2000 and 2003 it stands for C:\Documents and Settings\Current User\Start Menu\, and for Windows Vista/7 it is C:\Users\Current User\AppData\Roaming\Microsoft\Windows\Start Menu.
%CommonAppData% means the Application Data folder in the All Users profile. For Windows XP, Vista, NT, 2000 and 2003 it has the location C:\Documents and Settings\All Users\Application Data\, and for Windows Vista/7 it is C:\ProgramData.

Is this for real? This WIN thing is a virus in it self? Boy are they gonna make some money with this! I wish I had found this site a little sooner,I did purchase,but have not installed as of yet,aftyer reading this I’m a little undecided about installing. What other things out there are just to rob the public? Thanks,C.D.Moore