There are several ransomware-type applications that modify the “Shell” registry entry of your computer. The location of this “Shell” registry key is as follows – HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\. The default value of this “Shell” string must be explorer.exe, however, the scam perverted it by assigning the totally different name to it. The key to ransomware successful removal is in restoring the original value of “Shell” reg key. Here is your free guide how to do it.
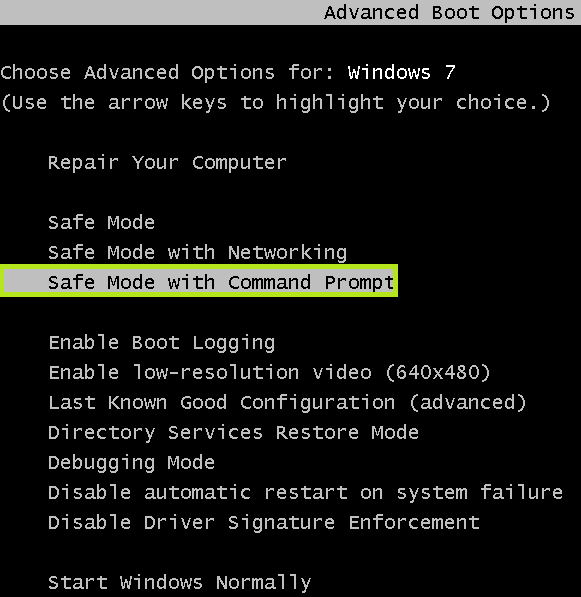
- Reboot your computer into SafeMode with Command Prompt. For this purpose please select “Restart” or “Reboot” option via Start menu. Before Windows starts booting start repeatedly hitting “F8” button on your keyboard. The following window comes up:
- Apply up / down arrow keys of your keyboard to select Safe mode with command prompt.
- Log into the same account you used when your computer became locked with ransomware.
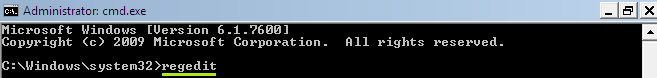
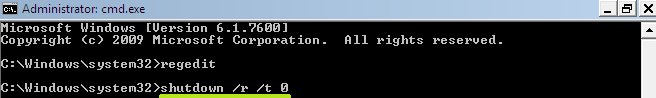
- In the window that came up type-in “regedit” and press “Enter“.
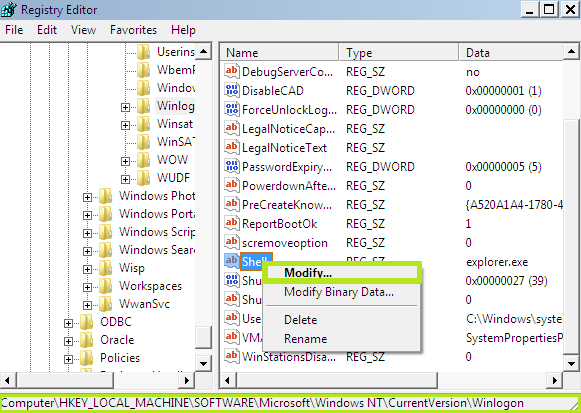
- The above-mentioned command opens the Registry Editor. Now locate the following path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\
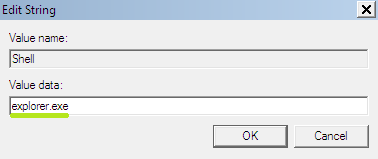
- In the right-side section find and choose the registry key named Shell. Right-click this registry key and choose Modify.
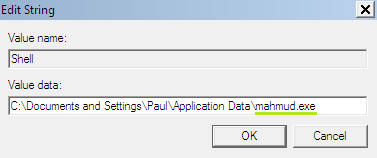
- Its value by default should be explorer.exe. However, the ransomware modified it in the following manner:
- Return this registry entry value back to “explorer.exe” as depicted at the screenshot below:
- Get back to “Normal Mode“. In order to restart your computer, at the command prompt, type the combination “shutdown /r /t 0” (without quotes) and press Enter button of your keyboard.
- Now, when the PC is successfully booted, please download reliable, effective and powerful anti-virus sofware recommended in this blog.
- Get rid of all detected infections.
- Consider installing certain anti-virus with real-time professional version that would be able to protect your PC from such malware attacks.
- However, if this solution didn’t help you, please consider using other guides to remove ransomware-type infections in the respective “Ransomware” category of this blog.
Comments are closed.