The fake warning supposedly originated by the New Zealand Police and its New Zealand E-Crime Lab is an Urausy ransomware virus infection. It primarily targets those PCs located in New Zealand. Yet, there are chances that other states will be attacked by this scam as well. The virus is presented in the form of a picture with logos and the names of these law enforcement organizations. The message claims to be also coming from Nga Pirihimana o Aotearoa, Centre for Infrastructure Protection (CCIP) and Interpol. The primary message of this scam is a condemnation with regard to the owner of the locked computer for committing various crimes online, thus supposedly explaining the reason for the locked status of the PC.
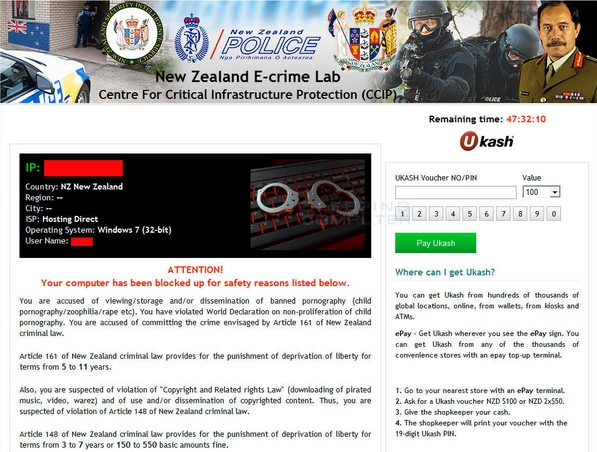
Never trust this warning, no matter how convincing it might seem to be. Here is what the fake Centre for Infrastructure Protection alert asserts once it attacks your computer:
New Zealand E-Crime Lab
New Zealand Police
Nga Pirihimana o Aotearoa
Centre for Infrastructure Protection (CCIP)
Interpol
Attention!
Your computer has been blocked for safety reasons listed below.
You are accused of viewing/storage and/or dissemination of banned pornography (child pornography/zoophilia/rape etc). You have violated World Declaration on non-proliferation of child pornography. You are accused of committing the crime envisaged by Article 161 of New Zealand criminal law.
Article 161 of New Zealand criminal law provides for the punishment of deprivation of liberty for terms from 5 to 11 years.
Also, you are suspected of violation of “Copyright and Related rights Law” (downloading of pirated music, video, warez) and of use use and/or dissemination of copyrighted content. Thus, you are suspected of violation of Article 148 of New Zealand Criminal Law.
Article 148 of New Zealand criminal law provides for the punishment of deprivation of liberty for terms from 3 to 7 years or 150 to 550 basic amounts fine.
It was from your computer, that unauthorized access had been stolen to information of State importance and to data closed for public Internet access.
The penalty set must be paid in course of 48 hours as of the breach. On expiration of the term, 48 hours that follow will be used for automatic collection of data on yourself and your misconduct, and criminal case will be opened against you.
Amount of fine is NZD $100. You can pay a fine Ukash vouchers.
As soon as the money arrives to the Treasury account, your computer will be unblocked in course of 24 hours.
Then in 7 day term you should remedy the breaches associated with your computer. Otherwise your computer will be blocked up again and criminal case will be opened against yourself (with no option to pay fine).
As you see, the primary plan of virus makers is to make users scared about their personal freedom. The accusation lists a large number of articles in the legislation where various illegal activities are condemned. The fake New Zealand E-Crime Lab tells that the user has been found guilty of performing such illegal activities. Then the locker says that user can even be put into prison for such crimes. As an alternative of being imprisoned, the virus offers users to pay the fine in the amount of NZD $100 and to avoid all negative consequences related to performing such fake illegal activities.
New Zealand E-Crime Lab virus instructs users to pay the fine through Ukash payment system. In reality, this is not a fine at all. This is a ransom which goes directly into the pockets of cyber frauds. Also, there’s no any guarantee from them that after user pays the ransom the computer will be unlocked.
If your computer has been locked by the New Zealand E-Crime Lab ransomware first thing you need to do is to ignore this fake alert on your screen. Remember that it has nothing to do with Centre for Infrastructure Protection (CCIP) or any other organization mentioned in the warning. In order to remove this locker from your computer please follow the instructions set forth below.
Recommended ransomware removal solution:
- Restart your computer into Safe Mode with Networking. To do it, keep hitting F8 key repeatedly, before Windows OS starts booting.
- Select your operating system and the account that got locked with ransomware.
- When Windows launches in Safe Mode with Networking, use “Win + R” hotkey combination to open Windows Explorer.
- In the address line insert the text “https://www.system-tips.net/download.php“
- Click “OK”.
- Download, install, update and run Plumbytes Anti-Malware.
- Scan your computer with Anti-Malware and remove all detected threats.
- Restart your computer.
- Share this information with your friends on Facebook and other social networks.
Similar removal video at YouTube:
So, we do recommend you to try the above method initially. Then, if it does not work, try these other guides below. It is probable that these other methods will be effective solutions to fix your problem. If this information has been helpful to you please share it with other friends of yours.
Alternative removal guides to remove ransomware from your computer:
- Ransomware removal in Safe Mode with Networking – https://www.system-tips.net/ransomware-removal-in-safe-mode-with-networking/
- Removal of ransomware that modifies “Shell” registry entry – https://www.system-tips.net/remove-ransomware-that-modifies-shell-registry-entry/
- Removal of ransomware that replaces explorer.exe file – https://www.system-tips.net/ransomware-that-replaces-explorer-exe-file-guide-to-unlock/
Optional ransomware removal through System Restore:
- Ransomware removal in Safe Mode with Networking – https://www.system-tips.net/ransomware-removal-in-safe-mode-with-networking/
- Removal of ransomware that modifies “Shell” registry entry – https://www.system-tips.net/remove-ransomware-that-modifies-shell-registry-entry/
- Removal of ransomware that replaces explorer.exe file – https://www.system-tips.net/ransomware-that-replaces-explorer-exe-file-guide-to-unlock/
Optional ransomware removal through System Restore:
https://www.system-tips.net/how-to-unlock-computer-though-system-restore-restore-point/
Optional similar virus removal video guide (through System Restore method):
Important! If the above-mentioned guidelines didn’t help you unlock your PC, use this guide as a final solution – http://www.bleepingcomputer.com/virus-removal/remove-your-computer-has-been-locked-ransomware
This has not worked after step 2 and 3
the computer shuts itself own before you can do anything