This guide explains termination of insecure.exe, the core process of Internet Security 2014 malware. Internet Security virus has been amended recently. So, now its desktop icon after installation of the rogue onto computers is titled as “Internet Security 2014”. Generally, simply adding “2014” didn’t change anything substantially. Yet, there’s another significant alternation that has been recently introduced by hackers into this rogue security program. The process “amsecure.exe” has been now replaced with “insecure.exe“. This is a crucial amendment, of course. The first step to successful removal of this malware is terminating its malicious process. Before we had to deal with “amsecure.exe”, but now we should pay attention to “insecure.exe” process. Specifying the name of this process correctly is the key to successful termination of the virus process.
There are various ways how computers can be infected with Internet Security 2014 virus. Obviously, in the online world these days there’s no 100% security against all possible threats which become modified on a regular basis. The primary goal of this scam is to bring money to its developers, who are surely the pack of cyber frauds. They want to get your money, and Internet Security is just the starting point from which they want to rip you off. Basically, as we’ve mentioned, outwardly the modifications implemented by cyber frauds with regard to this rogue application aren’t really visible, except for the icon name of Internet Security 2014 virus renewed in the following manner:
![]()
Now, the very rogue called Internet Security looks like this:
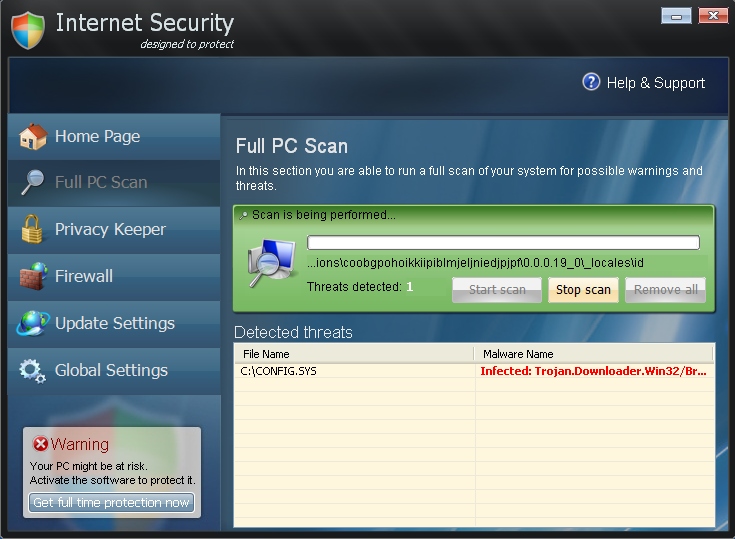
The malware’s goals and motives haven’t been changed. And this fact doesn’t surprise us. The malware developers have in mind to earn as much money as possible through deceiving simple computer users. They therefore use Internet Security 2014 as a tool for scaring users with a lot of deceitful information about various malwares supposedly detected by this scam. But remember that this application didn’t come to your system according to your instructions, right? It came on your PC suddenly, out of the blue. Plus, the rogue modified your system settings with the intention to be self-launched automatically each time you turn the computer on. Hence, many fake scans of Internet Security 2014 are inevitable. You will see the annoying window of this fake AV each time you want to use your computer. Obviously, this fact can’t be tolerated for a long time, and so users are in search for the correct solutions on removal of this scam off their computers. We hope that you will not purchase this scam. Instead, please follow the guidelines below that will help you get rid of this hoax from your system effectively.
Removal video at YouTube:
Steps one needs to undertake for removal of Internet Security 2014 scam:
- Click “Start” menu and go to “Run” option. Type-in the following text exactly as it is specified here:
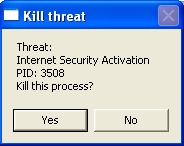
taskkill.exe /F /IM insecure.exe
This will stop the process of Internet Security 2014. (if you could not do it from the first attempt then try again)
- Download our recommended security software to your infected PC, install and run it.
- Remove all identified files and registry entries associated with the rogue anti-spyware, as well as other available threats.
Important! If this method didn’t help you kill the process of Internet Security virus, visit this guide https://www.system-tips.net/ruskill-exe-tool-to-kill-malware-by-window-title/ that will help you terminate the virus process using RusKill.exe application. Make sure you follow the instructions carefully!
Alternative way to terminate insecure.exe (Internet Security 2014 process):
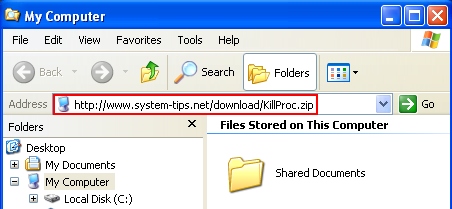
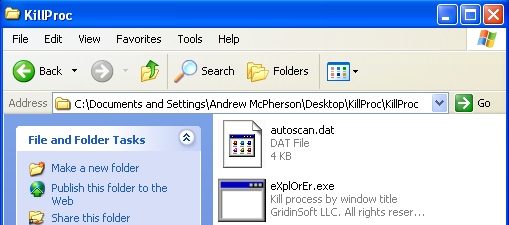
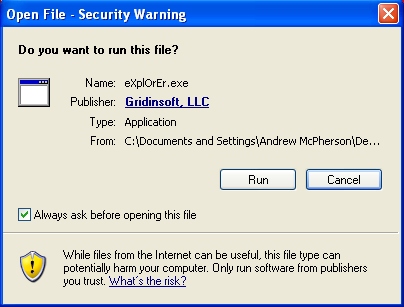

I can’t believe Trend Micro Titanium Internet Security did *not* catch this – on two different machines! Before reading this, I did find the “insecure.exe” file and deleted it. The new desktop icon pointed right to it. That made my PC somewhat usable *but* I think it changed some registry keys/values that no longer allow you to download *anything* – every download is ID’d as a “virus” and deleted (from *any* browser, tried IE and Chrome). I haven’t yet run any of the tools you have provided but if infected users have the same thing I have – they won’t be able to download any tools from the infected machine. They’ll have to do that from a clean machine. Thanks in advance for your help!