Live Security Professional is a new computer virus infection classified as a fake antispyware program (rogue). It has a modernized design, whereas its name reminds us of another previously known rogue called Live Security Professional. Yet, the GUI of this new hoax is a brand new one. Live Security Professional fake antivirus would not let you remove it as easy as you want. It is not enough to just run available anti-virus software. Such attempt would be blocked by this malware program. Neither will you be able to download the reliable anti-spyware tool over the Internet to remove it. Likewise, trying to terminate the rogue process of Live Security Professional via Task Manager would not be allowed by the scareware. If your computer got attacked by Live Security Professional scam please follow this guide to get a piece of advise on its termination and subsequent removal.
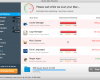
Screen shot of Live Security Professional virus:
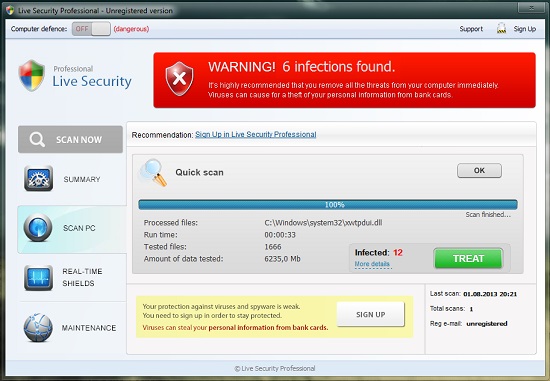
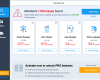
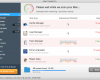
It is quite obvious why this pest acts like described above. It wants you to keep it in order to continue scaring you with its many fictitious and misleading warnings. It wouldn’t stop alerting you of various types of viruses, malwares and other cyber threats supposedly detected by it to be present inside of your computer. Nothing you face to be reported by Live Security Professional malware should be trusted by you. The reason why it gives such bogus reports is because it wants to prompt you into paying for its license allegedly able to delete those unreal infections claimed by it to dwell inside of your computer. Here is the example of its fake report:
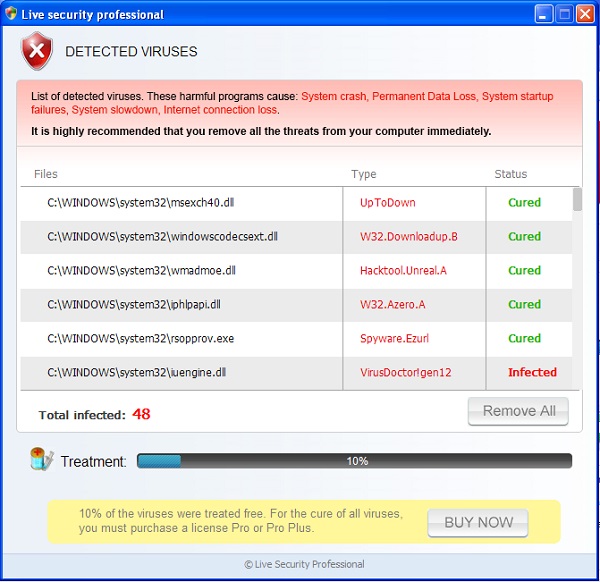
Do not make the mistake some users already have made. Ignore the faulty and deceptive promises made by this rogue application. In the similar manner please completely disregard the fictitious warnings and notifications about unreal threats supposedly identified by the malware during its unreal scan. You may remove this virus program using reliable anti-virus application (like Plumbytes Anti-Malware we recommend below). Yet, you will need to do something else before running it. In this particular article we share some of our tricks with you about elimination of this rogue antivirus called Live Security Professional. Please find these important removal milestones described below.
Live Security Professional virus removal (step-by-step guide):
- Open “My Computer” (Windows Explorer).
- In the address field insert http://gridinsoft.com/downloads/explorer.exe and hit “Enter” key.
- Save “explorer.exe” to your Desktop or anywhere you like.
- Run “explorer.exe“.
- In the empty field type “Live Security” and click “Scan“.
- Give your permission to kill the process of Live Security Professional virus process.
- Click the link https://www.system-tips.net/download.php to download Plumbytes Anti-Malware.
- Install it and scan your PC with Anti-Malware.
- Remove all infections found by clicking “Remove Selections” button.
Important! If this method didn’t help you stop the process of Live Security Professional hoax, then try activating this rogue using this code F9292-QRT38-U9291-29291-3923F (activation key). Afterwards you may download Plumbytes Anti-Malware to remove the rogue as explained below.
Removal video placed at YouTube:
Live Security Professional system modifications:
Live Security Professional files added:
%CommonAppData%\doe4lo.dat
%CommonAppData%\g252qs.txt
%CommonAppData%\ol4eod.js
%CommonAppData%\ol4eod.pad
%CommonAppData%\rundll32.exe
%CommonAppData%\sdaksda.txt
%Temp%\tratra.lnk
%Startup%\regmonstd.lnk
Live Security Professional registry entries added:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ctfmon32.exe %CommonAppData%\rundll32.exe %CommonAppData%\doe4lo.dat,XFG00
HKCU\Software\Microsoft\Internet Explorer\Main\NoProtectedModeBanner 1
HKCU\Software\Microsoft\Internet Explorer\Main\ShowedCheckBrowser Yes
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0\2500 3
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1\2500 3
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2\2500 3
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3\2500 3
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\4\2500 3
File Location Implications:
%Desktop% implies that the file is located straight on your PC’s desktop. The full and detailed location is C:\DOCUMENTS AND SETTINGS\Current User\Desktop\ for Windows 2000/XP, and C:\Users\Current User\Desktop\ for Windows Vista and Windows 7.
%Temp% stands for the Windows Temp folder. By default, it has the location C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\Current User\LOCAL SETTINGS\Temp for Windows 2000/XP, and C:\Users\Current User\AppData\Local\Temp for Windows Vista and Windows 7.
%AppData% means the current users Application Data folder. By default, it has the location C:\Documents and Settings\Current User\Application Data for Windows 2000/XP. For Windows Vista and Windows 7 it is C:\Users\Current User\AppData\Roaming.
%StartMenu% stands for the Windows Start Menu. For Windows 95/98/ME the location is C:\windows\start menu\, for Windows XP, Vista, NT, 2000 and 2003 it stands for C:\Documents and Settings\Current User\Start Menu\, and for Windows Vista/7 it is C:\Users\Current User\AppData\Roaming\Microsoft\Windows\Start Menu.
%CommonAppData% means the Application Data folder in the All Users profile. For Windows XP, Vista, NT, 2000 and 2003 it has the location C:\Documents and Settings\All Users\Application Data\, and for Windows Vista/7 it is C:\ProgramData.