In this article you will find helpful instructions to remove Antivirus System fake anti-spyware from your computer. If you have this scam on your PC please use these tips to effectively get rid of Antivirus System malware.
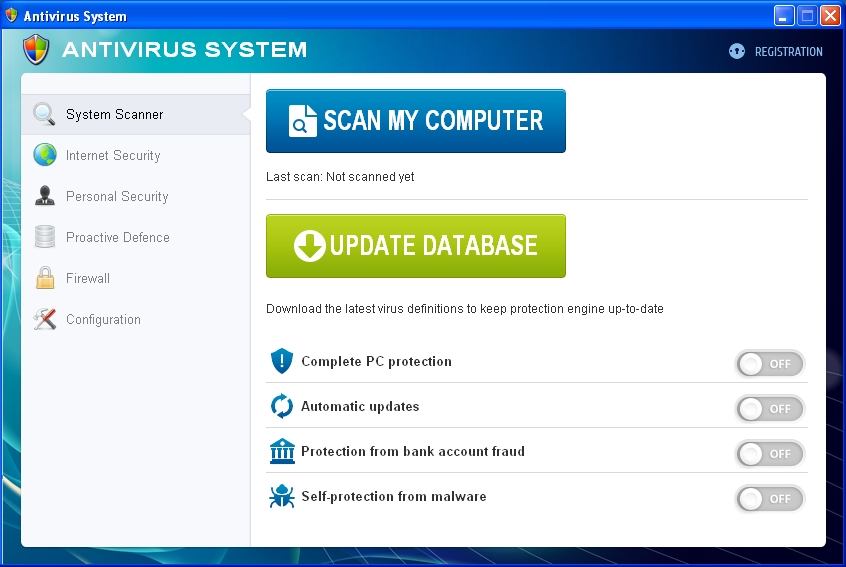
Antivirus System is a rogue antivirus software, in fact. It doesn’t come with installer or uninstaller, so you can’t easily remove it from your system through Control Panel in the section Add/Remove programs. The malware finds various leaks in your security settings and in legitimate security software already installed. Truly, there’s no absolutely 100% protection against latest security threats these days. As a result, Antivirus System scam may easily target your PC and get inside of it.
It is worthy to be mentioned that the very design of this scam is similar to that of PC Defender Plus (another rogue antivirus that was very much spread in 2012). Antivirus System hoax modifies your system settings in order to be self-launched automatically each time you turn your computer on. Immediately the rogue begins imitating scanning of your PC for various security threats and vulnerabilities. Obviously, this is a fake scan to make you scared tremendously about the condition of your computer. Once the bogus scan is completed the rogue reports the following threats supposedly detected by it:
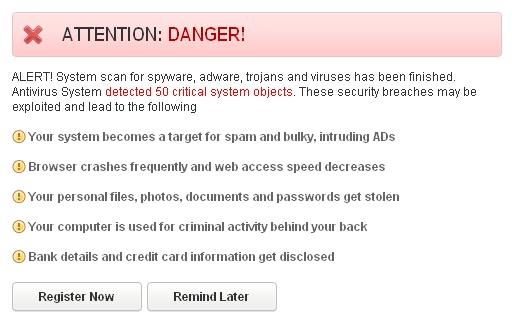
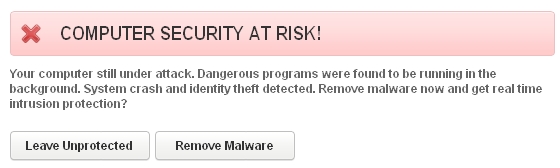
The fake scan of Antivirus System hoax runs quite quickly and reports huge amount of fake threats. Obviously, you should ignore this fake warning at the end of each fake scan of this rogue program. The scam will report that your computer security is at risk. Likewise, ignore this alert, please:
Antivirus System malware tries to imitate the behavior of Firewall, which is obviously a fake one. Here is the example of fake Antivirus System Firewall Alert:
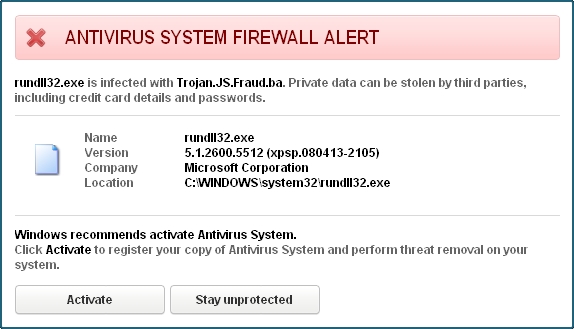
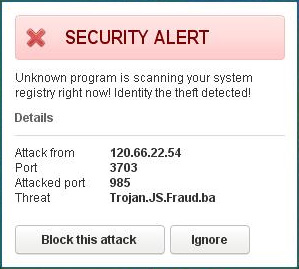
While the fake scanning of Antivirus System malware takes place, this hoax presents a lot of other fake and scary alerts, warnings and notifications about various fake threats supposedly revealed on your system (such as Trojan.JS.Fraud.ba as an example):
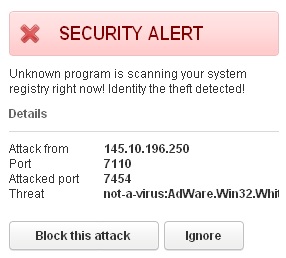
It also gives many other fake reports about bogus infections like Trojan-Clicker.JS.Agent.op, not-a-virus:AdWare.Win32.White Smoke.a and many other invented threats:
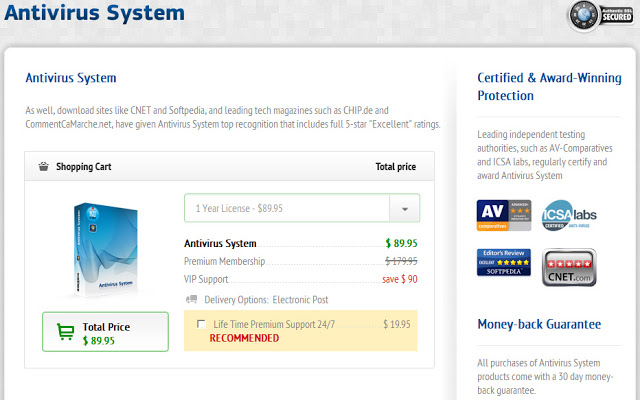
The reason why the rogue gives such a large number of fake security alerts, warnings and notifications is because it wants to scare users into buying it. Hopefully, this will never be the case with you. Ignore its fake payment processing page as shown below:
Hopefully, you will never buy this scam called Antivirus System. Instead, please carefully follow the malware removal instructions below.
Antivirus System removal instructions:
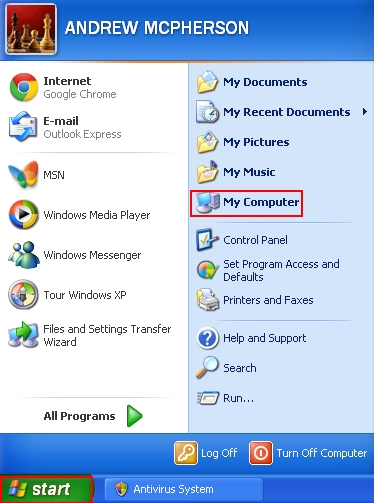
- For Windows XP, Vista or 7 click “Start” and go to “My Computer“. Alternatively, for all Windows versions (including Windows 8) you may use “Win + E” hotkey command to open Windows Explorer (a.k.a. “My Computer” or simply “Computer” as in Windows 8):
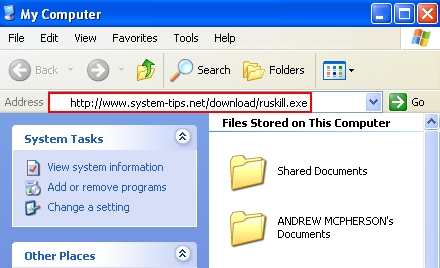
- In the address field insert the text for the download link of “ruskill.exe“:
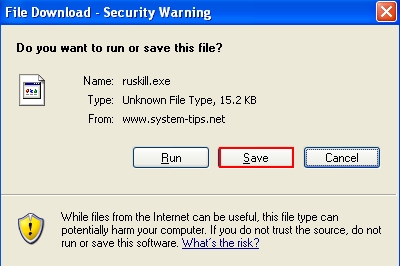
- Press “Enter” key on your keyboard, then click “Save” to save “ruskill.exe“.
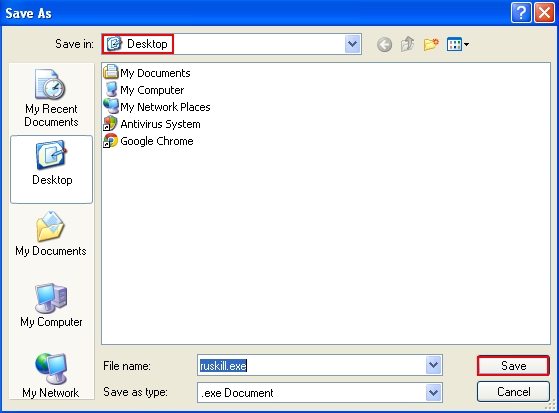
- Select “Desktop” as the destination to save “ruskill.exe“.
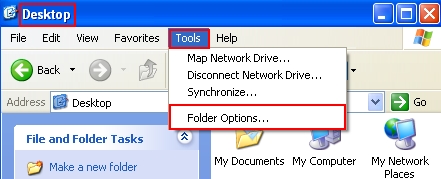
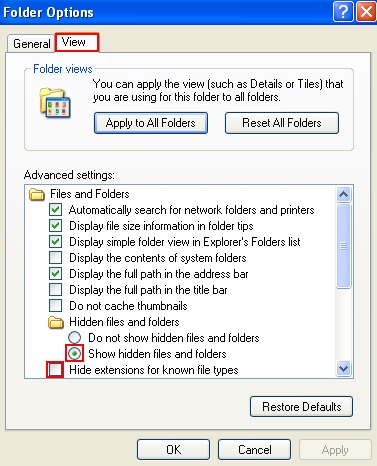
- In “Desktop” folder, click “Tools” and select “Folder options“. In Windows 8 click “View” and select “Options“:
- In the “View” tab make sure that you can see file extensions and hidden files:
- Click “OK“.
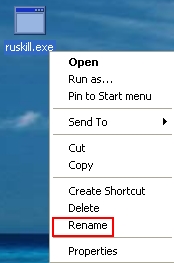
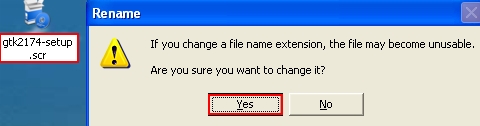
- On Desktop right-click “ruskill.exe” and select “Rename“:
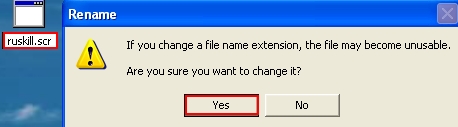
- Rename “ruskill.exe” to “ruskill.scr“. Click “Yes“:
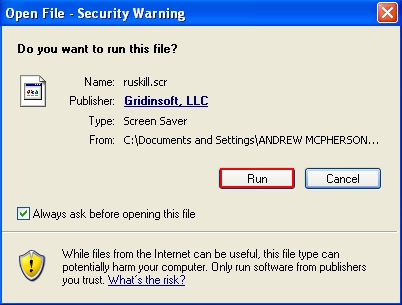
- Run “ruskill.scr“.
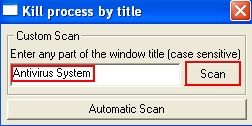
- In the open field type “Antivirus System” (with beginning capital letters, spacing and without quotation marks), then click “Scan“:
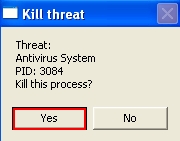
- The message will come up where you should agree to kill the process of Antivirus System scam:
- Open “My Computer” (Windows Explorer) as described above.
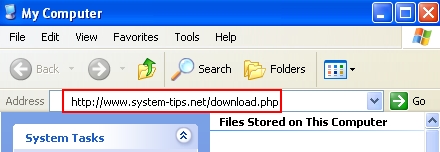
- In the address field insert the text for the download link of “Plumbytes Anti-Malware” – https://www.system-tips.net/download.php:
- Press “Enter” on your keyboard.
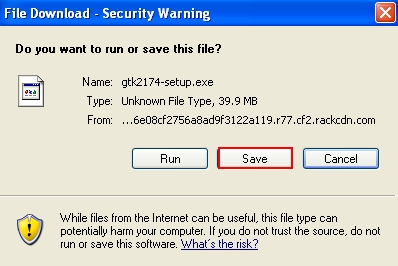
- Click “Save” to save Plumbytes Anti-Malware.
- Rename the installer of Plumbytes Anti-Malware with “scr” file extension (by right-clicking and choosing the Rename option). Click “Yes“:
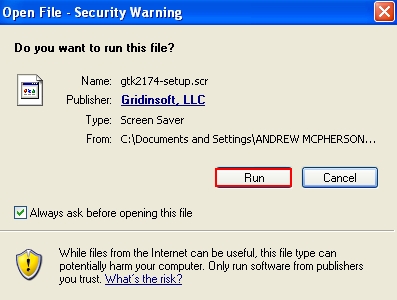
- Run renamed installer of Plumbytes Anti-Malware:
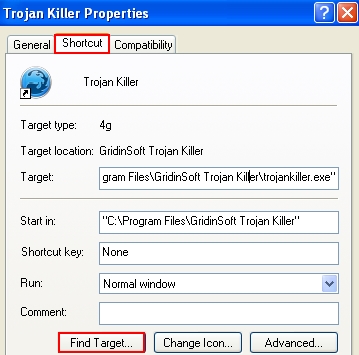
- Install the program (this may be done automatically by the installer). Find the desktop icon of Anti-Malware‘s executable. Right-click it and select “Properties“.
- Click “Find target“:
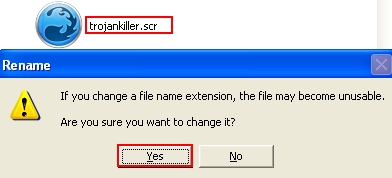
- Find “trojankiller.exe” and rename it into “trojankiller.scr” (by right-clicking the file and choosing such option):
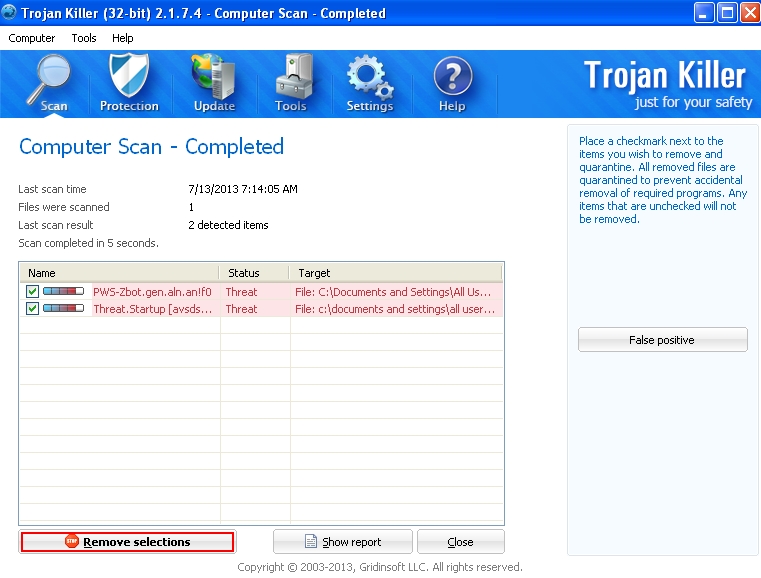
- Run “trojankiller.scr“. Scan your computer with Anti-Malware. Once the scan is completed click “Remove selections“:
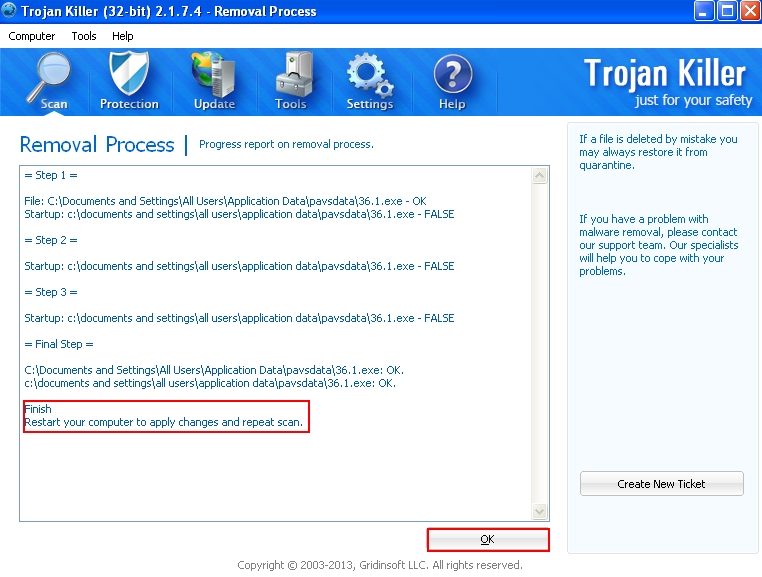
- It is recommended that you restart your computer and repeat the scan again.
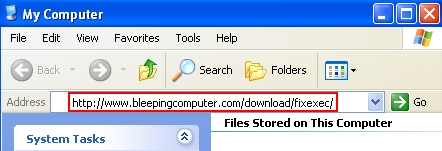
- In the address line of “My Computer” window type the following text: http://www.bleepingcomputer.com/download/fixexec/ and press “Enter“:
- Choose the appropriate version of FixExec utility (depending on your Windows version):
- Save FixExec to your Desktop.
- Rename FixExec extension from “exe” to “scr“.
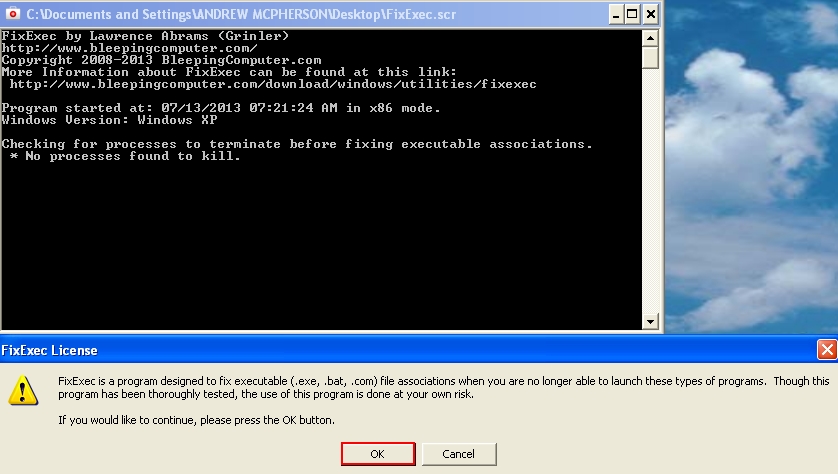
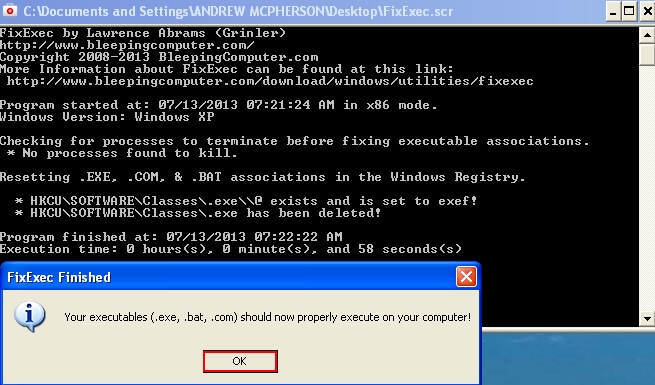
- Run FixExec.scr.
- Give your permission for the program do fix your executables (executable files):
- The problem with running executable files has been successfully solved:
![]()

Removal video at YouTube:
Antivirus System location:
If you right-click the desktop icon of Antivirus System rogue and click “Find target” you will see the location of the main executable file of Antivirus System scam. This location is a folder called “pavsdata” in Application Data directory:
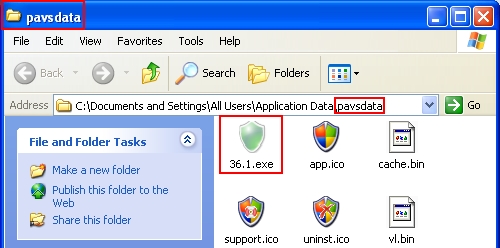
Files associated with Antivirus System hoax:
%AllUsersProfile%\Desktop\Antivirus System.lnk
%CommonAppData%\pavsdata\
%CommonAppData%\pavsdata\[number].1.exe
%CommonAppData%\pavsdata\app.ico
%CommonAppData%\pavsdata\cache.bin
%CommonAppData%\pavsdata\support.ico
%CommonAppData%\pavsdata\uninst.ico
%CommonAppData%\pavsdata\vl.bin
%CommonStartMenu%\Programs\Antivirus System\
%CommonStartMenu%\Programs\Antivirus System\Antivirus System Help and Support.lnk
%CommonStartMenu%\Programs\Antivirus System\Antivirus System.lnk
%CommonStartMenu%\Programs\Antivirus System\Remove Antivirus System.lnk
Associated registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\pavsdata
HKEY_CURRENT_USER\Software\Classes\.exe “(Default)” = “[random]”
HKEY_CURRENT_USER\Software\Classes\.exe “Content Type” = “application/x-m”
HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon “(Default)” = “%1”
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “(Default)” = “”%CommonAppData%\pavsdata\[number].1.exe” /ex “%1″ %*”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “avsdsvc” = “%CommonAppData%\pavsdata\[number].1.exe /min”
HKEY_CLASSES_ROOT\.exe “(Default)” = “[random]”
HKEY_CLASSES_ROOT\.exe “Content Type” = “application/x-m”
File Location Implications:
%Desktop% implies that the file is located straight on your PC’s desktop. The full and detailed location is C:\DOCUMENTS AND SETTINGS\Current User\Desktop\ for Windows 2000/XP, and C:\Users\Current User\Desktop\ for Windows Vista and Windows 7.
%Temp% stands for the Windows Temp folder. By default, it has the location C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\Current User\LOCAL SETTINGS\Temp for Windows 2000/XP, and C:\Users\Current User\AppData\Local\Temp for Windows Vista and Windows 7.
%AppData% means the current users Application Data folder. By default, it has the location C:\Documents and Settings\Current User\Application Data for Windows 2000/XP. For Windows Vista and Windows 7 it is C:\Users\Current User\AppData\Roaming.
%StartMenu% stands for the Windows Start Menu. For Windows 95/98/ME the location is C:\windows\start menu\, for Windows XP, Vista, NT, 2000 and 2003 it stands for C:\Documents and Settings\Current User\Start Menu\, and for Windows Vista/7 it is C:\Users\Current User\AppData\Roaming\Microsoft\Windows\Start Menu.
%CommonAppData% means the Application Data folder in the All Users profile. For Windows XP, Vista, NT, 2000 and 2003 it has the location C:\Documents and Settings\All Users\Application Data\, and for Windows Vista/7 it is C:\ProgramData.